
Akira - Ransomware-as-a-Service
This is part of a series focusing on the presentations from the Netnod Tech Meeting 2024. Each blogpost aims to summarise the key points from the presentation and provides link for readers who want to know more.
Ransomware-as-a-Service
Ransomware has always been around. The new kid on the block is Ransomware-as-a-Service (RaaS), where an end-user pays for a targeted attack. The presentation went through the stages of one such RaaS by Akira.
The approach
The attack chain is grounded in an initial exploit, in this case CVE-2020-3259, which gave the attackers access to credentials to the VPN-service, thus allowing VPN logon.
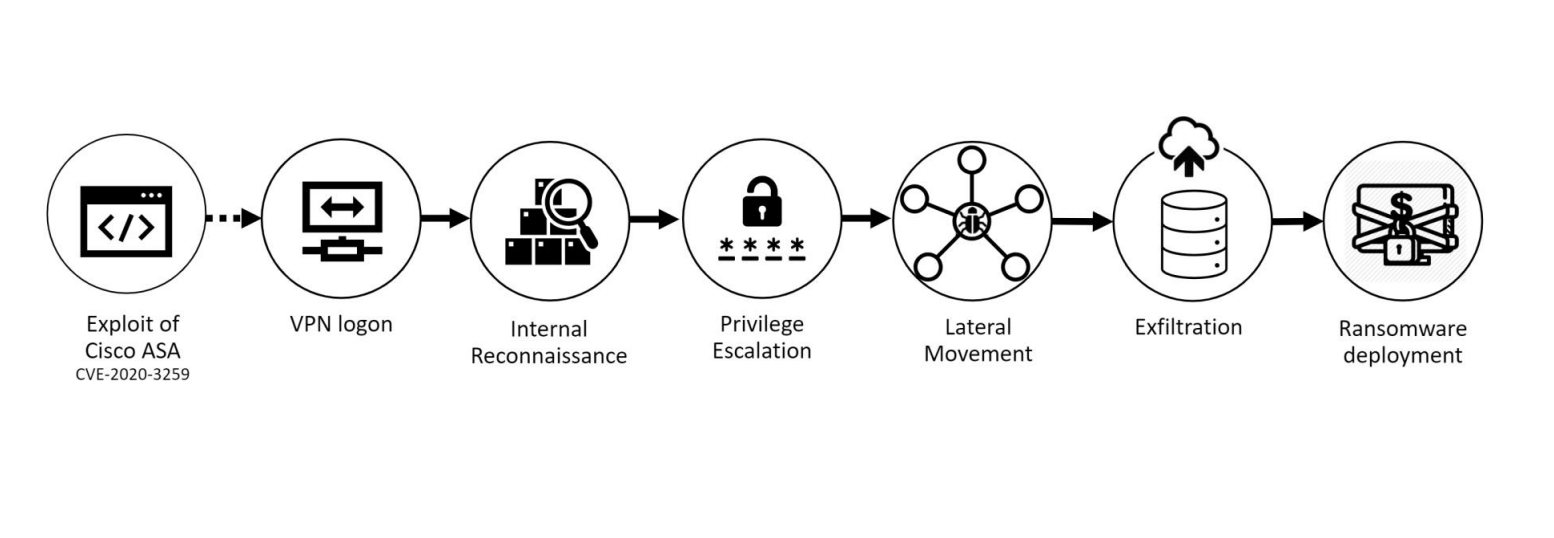
Figure 1: The attack chain as presented. Image courtesy of Truesec
After gaining access to the network, the attackers started enumerating the network (“Internal Reconnaissance” in Figure 1) in order to create an inventory of resources available to the attacker. Any open or unsecured resources in the network would allow for lateral movement.
After finding a vulnerable service, the attacker was able to escalate privileges to admin level (“Privilege Escalation”), which further increased the possibility of lateral movement within the targeted organisation.
Now, up until this point, the attacker has only used tools available and used by authentic administrators. This makes it almost impossible to distinguish an attacker from a real administrator managing the network or infrastructure (and proves false the misconception that firewalls protect against all malicious activity).

The first sign that something is off is the installation of software for persistence, in this case AnyDesk.
Heresh and Viktor point toward the importance of tiering and segmenting accounts. The advice is for administrators to use different accounts for different tasks across different systems and to avoid using accounts with high authorizations to move within the internal environment as this would open up the possibility of privilege escalation if an unauthorised user gets into the environment.
In this particular case WinSCP, Rclone and similar tools were used for exfiltration of data from the attacked systems (“Exfiltration”). Exfiltration normally contains both user account data (such as a copy of the Active Directory-service) and company data (such as data and documents in shared storage and folders).
Further down the line, the attackers deployed ransomware via Windows and ESXi. Encryption of the attacked systems was done through normal tools, such as the SMB-protocol from admin-user accounts on administrator machines.
The exploitation in turn refers the victim to contact Akira and pay a ransom fee, which usually is quite steep. If the victim does not pay the ransom fee, Akira will sooner or later leak the files and material stolen from the attacked organisation. The presenters recommend against paying the ransom and, instead, focusing on securing your network against such an attack in the first place.
Summary
In short, the presentation covers a typical Ransomware-as-a-Service (RaaS) attack, based on real life experience of working on the investigative side of the effects of these types of attacks.
It is hard to defend yourself against vulnerabilities in devices you buy. So you should focus on matters you control, such as segmenting user accounts so that no single user, or group of users, can perform all activities that would enable a successful exfiltration and exploitation attempt.
You can watch the full presentation here and see the slides here.




