
Is QKD or PQC ready to quantum secure optical networks?
This is part of a series focusing on the presentations from the Netnod Tech Meeting 2024. Each blogpost aims to summarise the key points from the presentation and provides links for readers who want to know more.
Post-Quantum Cryptography
We are currently on the threshold of going from conventional cryptography to quantum safe cryptography. To phrase it a bit differently, modern conventional cryptography is based on computational security of extremely hard (for normal computers) mathematical problems. Quantum computers change this equation, so that problems which are extremely difficult for conventional computers to solve become trivial.
Post-Quantum Cryptography (PQC) refers to algorithms used by conventional computers, which are hard / impossible for quantum computers to crack. On the downside, many PQC-algorithms for conventional computers require large public key sizes. This can be problematic in certain scenarios, such as security for IoT-devices with limited memory or DNSSEC where record size is limited in UDP-packets.
PQC is in general done as an end-to-end-solution, that is by the end-user through program suites and protocols such as TLS, HTTPS, SSH, and similar. In contrast, quantum key distribution is based on a set of larger trusted nodes, and not end-user devices or servers yet, due to the limitation of the current implementation.
Quantum Key Distribution
Quantum Key Distribution (QKD) refers to using quantum mechanics in the encryption process of keys. This means conventional computers, and network equipment, cannot decrypt QKD.
Is Quantum Key Distribution ready?
Fundamentally no; standardization, implementations and evaluations are still ongoing and taking time (Jim Zou)
QKD is considered by means of a special-purpose technology, even if mature, as it is based on dedicated equipment on the physical layer and still requires other security features (e.g. authentication, protection, etc.) to provide end-to-end security. As such, QKD is not supposed to replace the need for end-to-end-encryption.
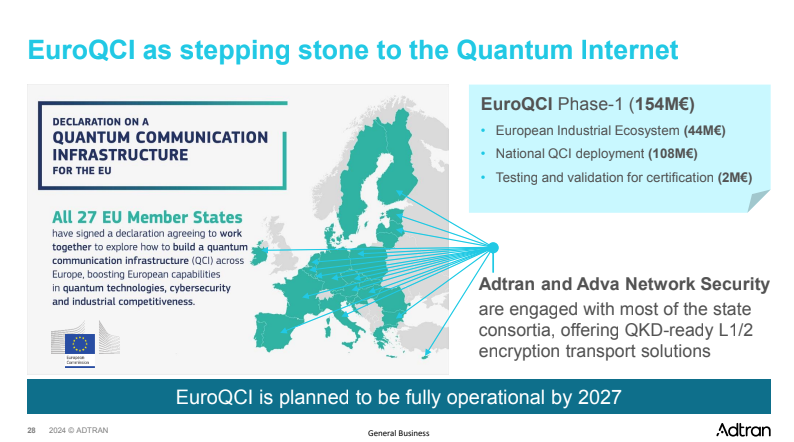
Slide from Jim Zou’s presentation at the Netnod Tech Meeting 2024. Reproduced with permission.
EuroQCI, an EU-financed initiative, is currently providing a significant amount of funding for research activities within the QKD umbrella.
Securing networks in a post-quantum world
The best approach is likely based on hybrid key exchange, where end-users’ organizations may adopt the PQC-algorithms and -keys used for exchanging the session key for end-to-end-encryption, while the network operator could offer an encryption service for optical traffic using hybridized keys from both PQC key exchange and QKD, to maximize the network security resilience.
Post-quantum encryption is not only about confidentiality, but also concerns the integrity of traffic, and more, while the QKD in particular has a role to play in a complementary physical security for the key exchange.
More information
You can watch the full presentation here and see the slides here.




